Alerts Investigation
Monitoring for new alerts is a critical activity for both the security and operations personel. This section explains how to use ADS to investigate a device alert.
See also the related Critical Alerts Screen documentation.
Investigate alerts
- Click on the specific alert on the Critical Alerts screen to view the alert details (Investigate screen):
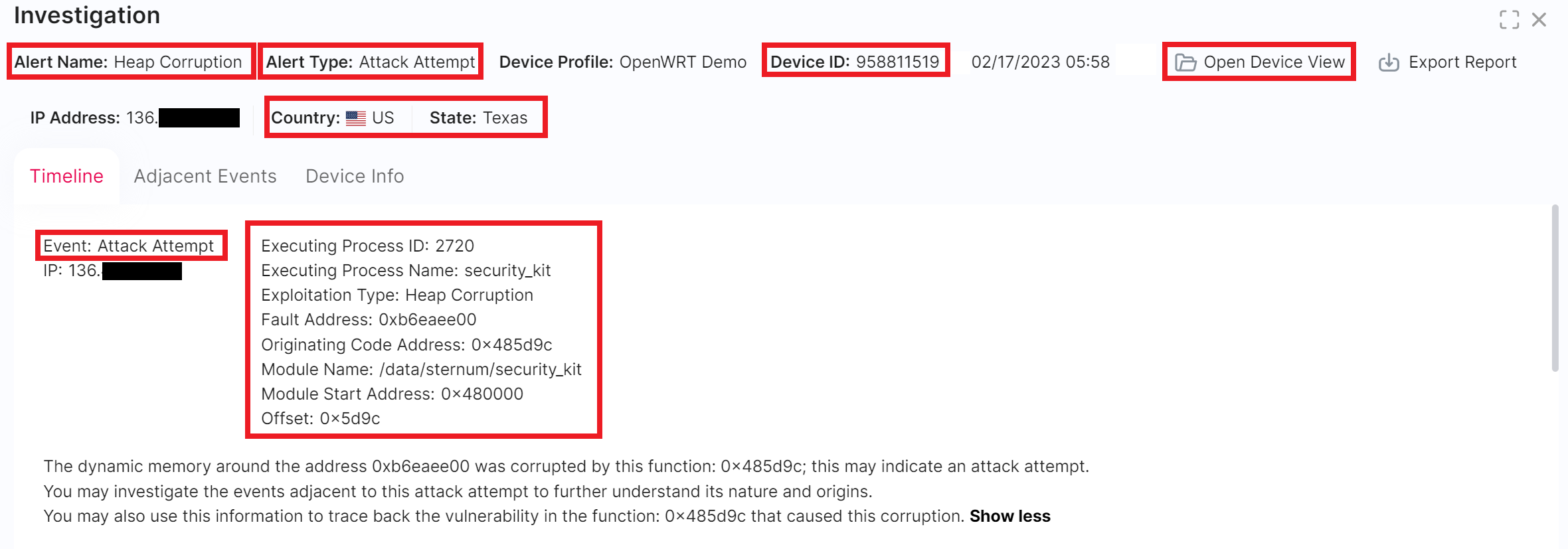
- Alert Name and Alert Type: Identify the type of alert
- Device ID: Identify the device that generated that alert
- Open Device View: Navigate to the device details screen
- Country /State fields: Verify the expected location of the device if known
- Timeline: Investigate events that lead to or triggered the event associated to the alert
Use the arrows on both sides to navigate the history of events.
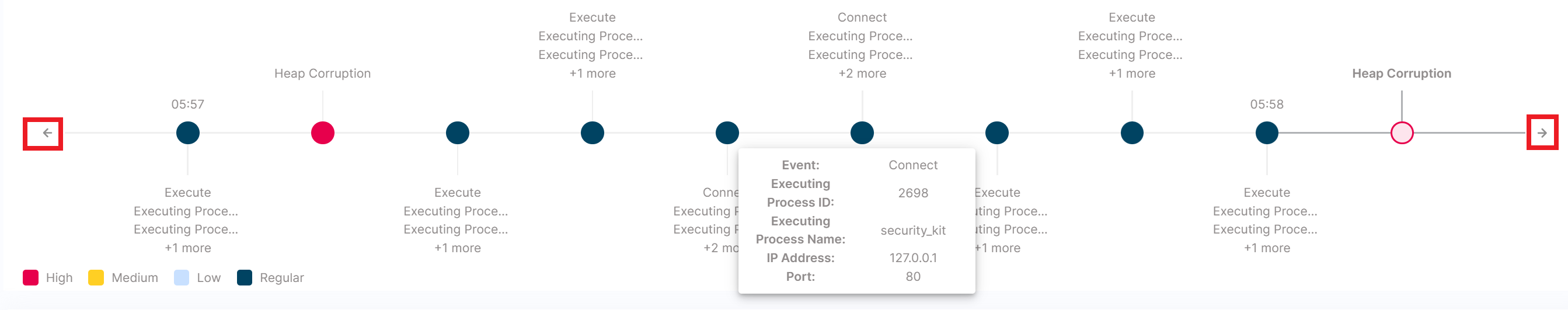
Click on each event to see the full event details.
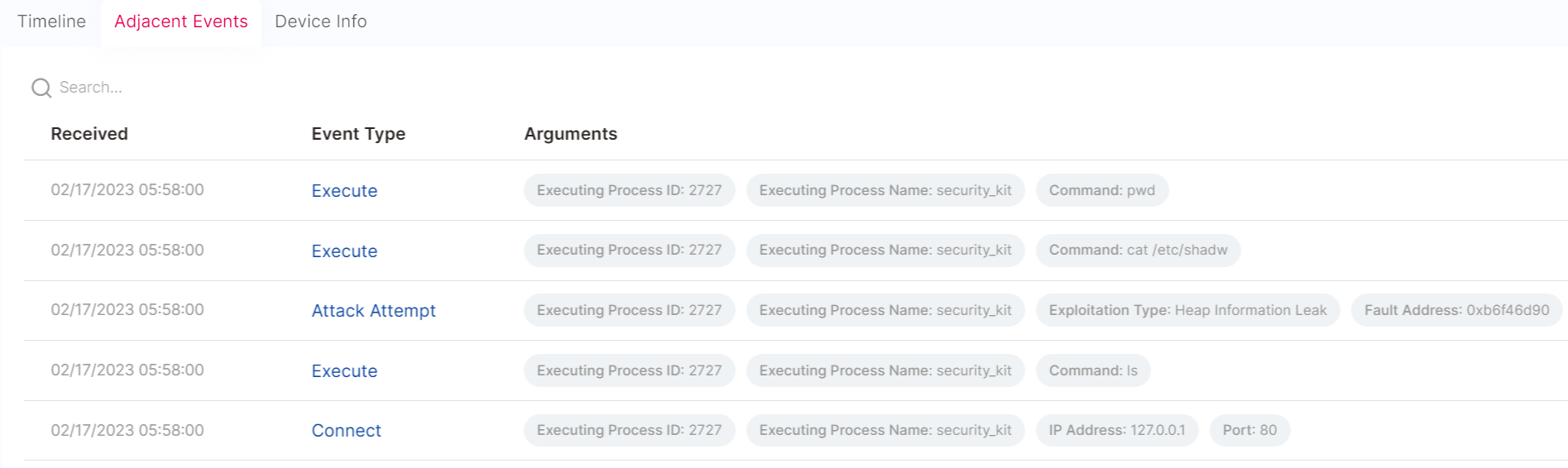
- Adjacent Events:view other events that may or not be related to the event associated with the alert. Use pagination to navigate through all event pages.
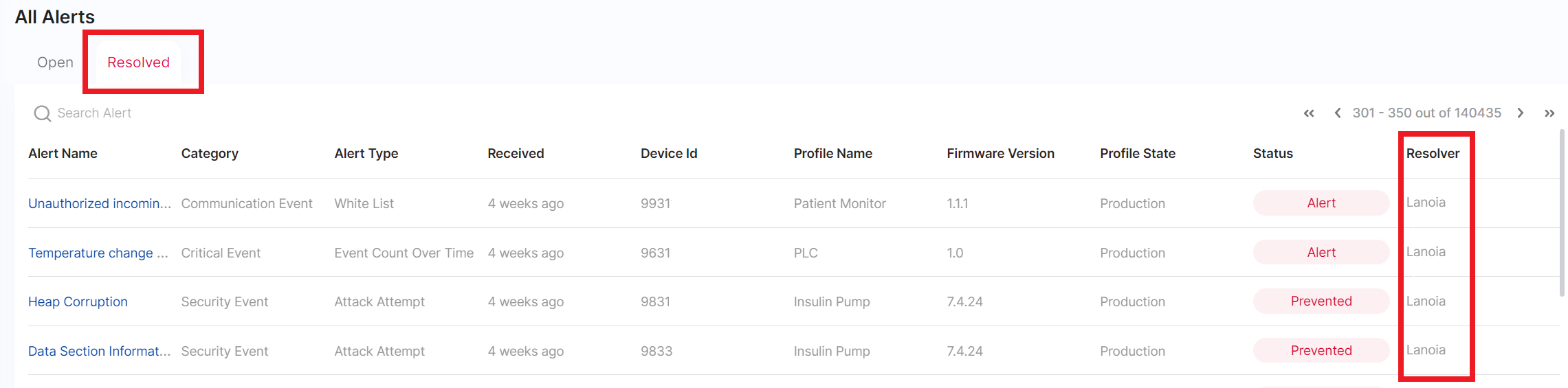
- Choose Export Report to generate a report if you want to share the alert information offline.
- Click on Resolve if you want to tag this alert as resolved. Resolved alerts are filtered out of the Open tab alert list but are accessible on the Resolved tab along with the user who resolved them.
Alert Types
Attack Attempt Alerts
This type of alert reports a security attack detected and prevented by EIV in the device. The alert provides the following information:
- Type of exploitation, for example:
- Heap Corruption
- Stack Corruption
- Data Section Corruption
- Name of the function (if identified) and address in memory where the attack originated from
- Address of the memory fault
ADS-generated Alerts
ADS analytics uses the data collected from EIV in the devices to detect potential device threats and anomalies and generates associated alerts. Example of such alerts could be:
Anomaly Alerts
These alerts are generated by ADS anomaly detection engine when it detects a variation of the device's expected behavior.
Firmware Update Anomaly Alert
Multiple initiations of the firmware update procedure were detected over a short period of time. This may indicate an attack attempt or trouble completing an update.
Updates Validation Alert
Multiple failures of firmware validation procedures were detected over a short period of time. This may indicate an attack attempt or trouble completing an update.
Multiple Login Failure
Multiple failed login attempts detected over a short period of time. This may indicate a brute force attack.
Anomalous behavior - high communication compared to average, multiple reboots etc
Custom Alert Types
Custom alerts are defined by users. See Custom Alerts.