Protect the Device
This section explains the general process to integrate Sternum RTOS EIV to provide runtime protection to the device.
General Process
The general development process to add runtime security into a RTOS-based firmware is shown on the figure below. If the device does not have any connectivity or will be deployed without communication to the Sternum Platform, please skip this section and read the Case of non-connected devices section instead.
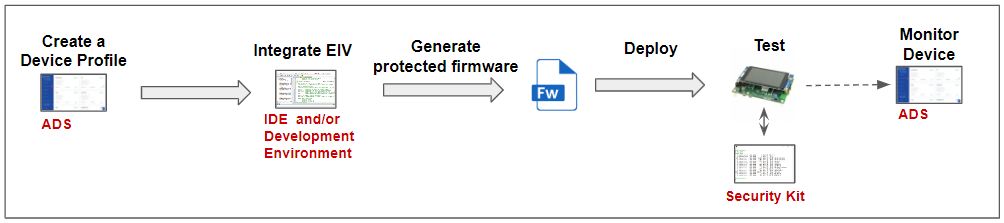
The general steps are:
- Create a Device Profile on the Sternum Platform to model the device and the current version of the firmware
- Integrate the RTOS EIV package into the development environment and firmware
- Generate a protected firmware
- Deploy (flash) the protected firmware to the device
- Test the protected device
- Monitor the device and security alerts on ADS.
Create a Device Profile on the Sternum Platform
The concept and creation of a device profile for the device and firmware are documented in the Onboard Device section of the Sternum Platform's Getting Started guide.
Integrate RTOS EIV
The general steps to integrate RTOS EIV are:
- Install the RTOS EIV package
- Configure the development environment
- Customize the adaption layer if required.
The integration of EIV is performed as an additional post-processing build step. This means that the EIV runtime component is integrated after the firmware binary has been generated (after compilation/linkage) by your build process (IDE, make/scripts or CI/CD). The EIV tools will analyze the firmware binary, add instrumentation and integrate the Sternum runtime protection mechanisms directly into the binary, then generate a protected firmware binary.
The installation and integration depend on the specific RTOS and development environment/IDE. Refer to the integration documentation.
Porting and customization of RTOS EIV adaptation layer
The typical customization tasks in the porting layer for the integration into RTOS devices is to: 1) Set the Device Definition ID to use 2) Implement how the device ID is set/retrieved.
Sternum provides a default port implementation for most RTOSs, which you can use as-is or customize per your specific needs. Refer to the Integration documentation for details.
Generate a protected firmware
Once the above one-time integration is performed, the build environment can automatically run Sternum tools to generate a firmware binary with embedded EIV runtime protection. Refer to the specific integration in the Integration sections.
Deploy the protected firmware
Flash the generated protected firmware to the device and reboot it. The device is now protected by EIV.
Test the device
Standard testing
Run the general device functional, system and performance tests to validate that EIV does not impact any function of the device.
Security testing
Use the Sternum Security Kit against the device to test the runtime protection provided by EIV.
The Security Kit contains a set of the most common attacks against IOT devices. The kit provides the source code to adapt the tests to the device characteristics (e.g. communication with the device or triggering of the attacks).
Refer to the RTOS Security Kit documentation provided in the EIV package for more information.
Monitor the device and security alerts
Once the device boots with the protected firmware, EIV automatically monitors for attacks and will send a security alert upon any detected attack to the Sternum Platform. Any implemented traces will also be sent automatically to the Sternum Platform (see Enable Observability).
Refer to the the Sternum Platform's Getting Started and View Device Alerts sections.
Case of non-connected devices
Devices with no connectivity (e.g. with no communication interface or when their deployment do not allow connectivity or communication to the Sternum Platform) do not require any Sternum Platform configuration.
For these devices, the development process is simplified:
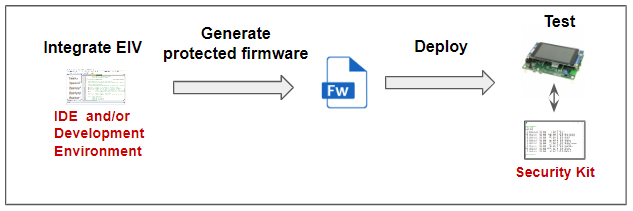
Refer to the above sections for the details of each step:
- Integrate the RTOS EIV package into the development environment and firmware,
- Generate a protected firmware
- Deploy (flash) the protected firmware to the device
- Test the protected device.
As explained in the Runtime protection-only section, a user callback function is available to add custom logic to be invoked upon detection of an attack. This mechanism should be used to perform any corrective or local notification to a user via any available interface.