RTOS EIV
The RTOS Embedded Integrity Verification (EIV™) ensures the integrity of the stack, the heap and the execution flows, making RTOS and baremetal devices immune to the most common cyberattacks. EIV ensures that the integrity is being kept not only on the device’s application code, but also for compiled code from third-party libraries, operating systems, communication stacks and SDKs, thus effectively protecting the entire device.
RTOS EIV is embedded into your firmware for deterministic runtime protection. When detecting and preventing a security attack, EIV automatically generates a security alert, which is sent to the Sternum Platform with the attack details. A C callback function can also be invoked to customize the local response by the device to the prevented attack (e.g. reboot, task restart) .
Adding EIV to a RTOS firmware is performed by a transparent post-build process that requires no coding and no need to access to the device source code for pre-integrated RTOSs (e.g. Zephyr, FreeRTOS). EIV provides a thin integration layer for adapting to other RTOS, embedded SDKs or barebone implementations.
EIV integration
The following diagram shows how EIV instruments the firmware for protection:
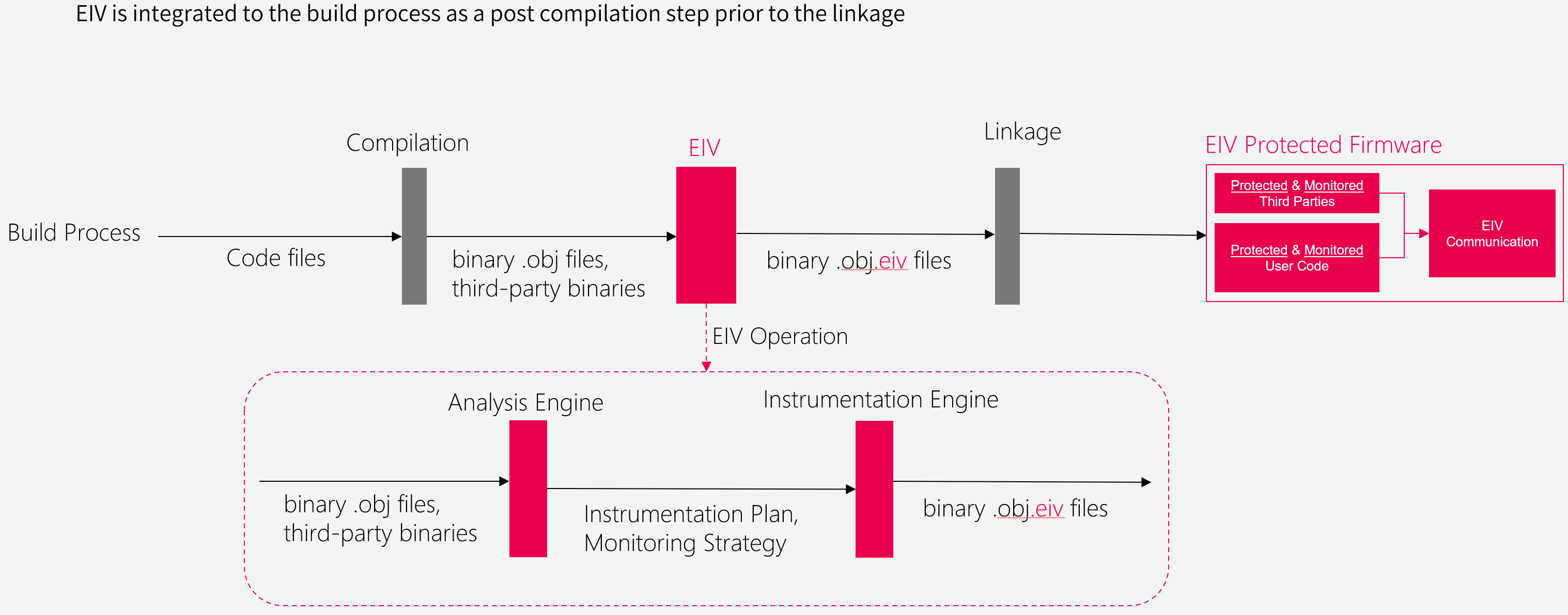
This Getting Started provides an introductory guide to the key Sternum EIV functionality for RTOS devices, including the integration of EIV into the device firmware, implementing traces using the EIV SDK, developing a Relay application for relaying traces in the case of devices that cannot directly communicate with the Sternum Platform, deploying devices and using the Sternum Platform to view security alerts and traces.