Linux EIV Introduction
The Linux Integrity Verification (EIV™) ensures the integrity of the the heap, the execution flows and shell command execution, making Linux devices immune to the most common cyberattacks. EIV ensures that the integrity is being kept not only on the device’s application code, but also for compiled code from third-party libraries, operating systems, communication stacks and SDKs, thus effectively protecting the entire device. EIV can also report about stack corruption if the binaries have been compiled with the proper related flags (e.g. -fstack-protector option on GCC).
EIV is embedded into your firmware. Deployment of EIV to your Linux firmware can be done via a simple installation script at build or runtime or by deploying the EIV artifacts when building the Linux image.
EIV deployment requires no coding and no access to the device source code.
System Architecture
The following diagram shows the system archicture with Linux EIV and the Sternum Platform:
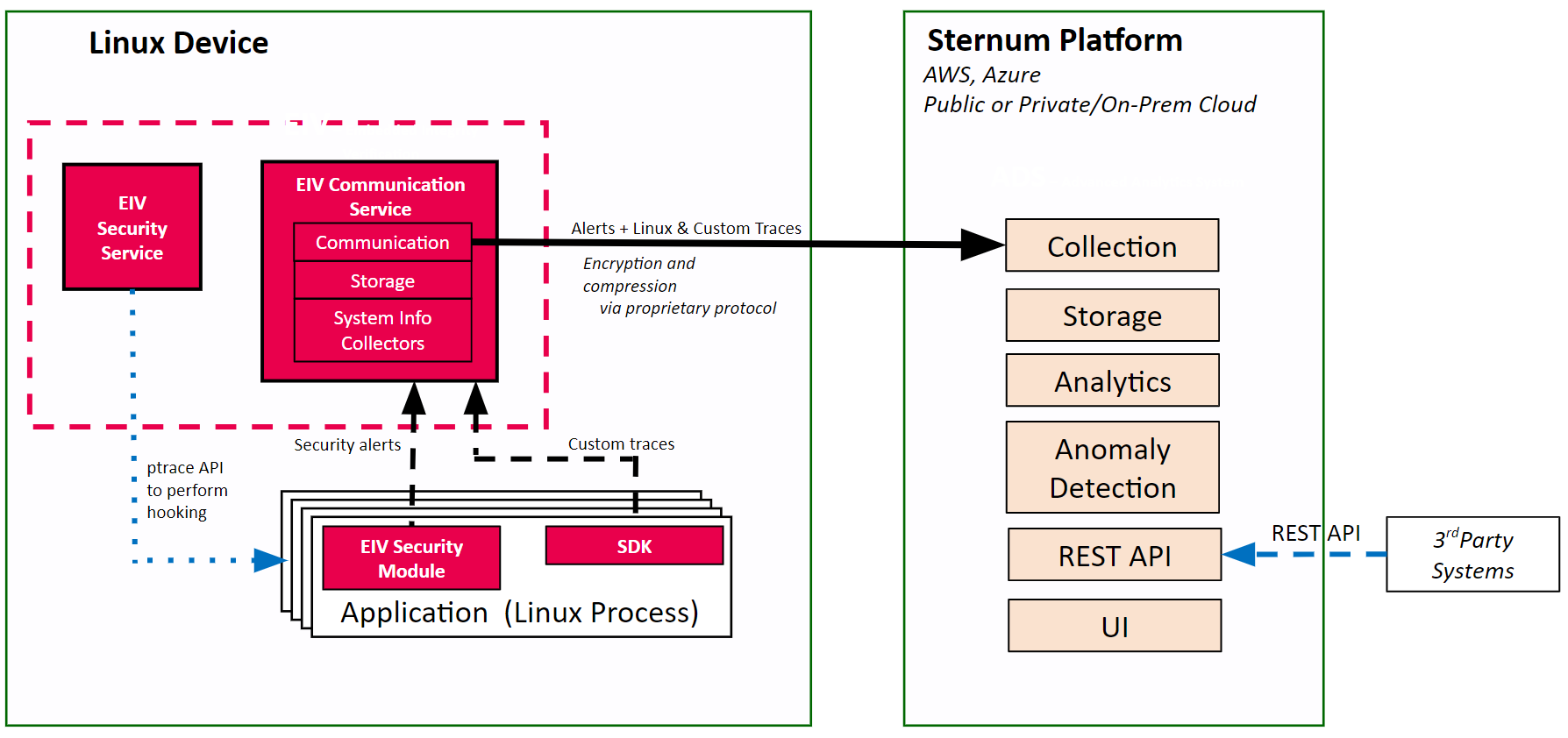
The next section describes the device requirements and how to deploy Linux EIV to your devices. You may also want to read about how to add observability capability to your Linux device and applications using the Sternum SDK to support enhanced security and troubleshooting.