EIV Overview
Embedded Integrity Verification (EIV™) is a first-of-its-kind, patented technology that offers a holistic security solution for IoT and embedded devices. Among its many capabilities, EIV ensures the integrity of the stacks, and the execution flows, which de facto makes the device immune to the most common cyberattacks. EIV ensures that the integrity is being kept not only on the device’s application code, but also for compiled code from third-party libraries, operating systems, communication stacks and SDKs, thus effectively protecting the entire device.
The Sternum SDK - aka. observability SDK, ADS SDK or simply SDK - works alongside EIV and enables the developers to add traces in the device firmware source code. Traces allow to send any kind of data, such as system, environment, user or performance metrics, log data, etc. to the Sternum Platform platform in order to facilitate the monitoring of devices and the investigation of device security and operational issues, as well as bugs.
System Components
EIV - Sternum's component that is embedded into the device firmware for deterministic runtime protection. When detecting and preventing a security attack, EIV automatically generates a security alert, which is sent to the Sternum Platform with the attack details. A callback mechanism can also be invoked to customize the local response by the device to the prevented attack (e.g. reboot, task restart) .
EIV is designed for simple integration to the target firmware. It requires no coding and no need to access to the device source code for pre-integrated platforms (e.g. Linux or common RTOS such as Zephyr and FreeRTOS). For other platforms such as custom Linux, other RTOS, embedded SDKs or barebone implementations, EIV provides a thin porting/integration layer.Sternum SDK - Allows to send device metrics, statistics, logs, etc. data to the Sternum Platform using a simple API available in C and Java. It supports connected and semi-connected devices and provides optimized tracing, caching and lightweight, secure and reliable data transfer to the Sternum Platform.
Relay - The Sternum SDK also provides the Relay functionality used by applications that interface and collect EIV alerts and/or data from devices that cannot directly communicate to the Sternum Platform (such as devices using bluetooth, non-TCP/IP or proprietary protocols), and forwards this data to the Sternum Platform via internet/intranet. Such applications typically run on an smartphone or on an IOT/Edge gateway device.
Sternum Platform - Sternum's cloud-based analytics and detection system (also known as ADS) collects security alerts and trace data from the devices protected and instrumented by EIV and the SDK and provides monitoring, custom analytics, dashboards, alerting and device anomaly detection functionality. The Sternum Platform is used by security engineers, operations teams, product managers and developers to monitor device security and operations, understand how devices perform thoughout their entire lifecycle, and learn how the users interact and use the devices.
Deployment use cases
Most device deployments use EIV, the Sternum SDK and the Sternum Platform together. However in some cases, some Sternum components or features are not used. The most common use cases are described below. One or more use cases can apply to the same device.
Runtime protection-only
In some deployments, devices cannot be connected to the Sternum Platform. This is the case for example when devices have no communication interface, are deployed in air-gapped environments, or when there is no communication network or path to the Sternum Platform.
Although there is no Sternum Platform where security alerts generated by EIV can be sent to alert the monitoring personel, EIV provides a mechanism to invoke some customizable device logic when an attack is detected. The custom logic can for example perform a restart of the task impacted by the attack, perform a smooth device shutdown or reboot, or alert the device operator via the device user interface (e.g. via user display, LED, or buzzer/speaker).
As there is no communication interface nor any Sternum Platform deployed, devices cannot be monitored remotely.
Runtime detection-only
For some critical industrial, transportation or sensitive real-time devices, it may be more important to detect and report rather than stopping an attack. EIV allows the runtime protection to be disabled if only attack detection and reporting are desired.
Device runtime protection and observability
This is the most common use case: Both EIV, Sternum SDK and the Sternun Platform are used together to offer runtime security, detection of device attacks and abnormal behaviors, device anomaly detection, custom dashboards and alerting.
Device observability only
The Sternum SDK is available for most Linux, RTOS or barebone platforms, allowing to provide device observability, abnormal behavior and threat detection, custom dashboards and alerting with the Sternum Platform. Android and iOS applications can also be monitored.
Device indirect communication - Relay applications
Some devices do not use the typical TCP/IP protocols but may for example use Bluetooth (personal devices), CAN (automotive or industrial devices), industrial or building protocols (Modbus, Profinet, BACnet, etc.), serial, radio or other proprietary protocols.
They connect to an intermediary system to communicate to the cloud, for example a smart phone application or an IOT, edge or gateway device of some sort.
In this situation, the devices embedding Sternum require the intermediary system to run the Relay function to forward the EIV alerts and SDK traces to the Sternum Platform. This Relay function is also provided by the Sternum SDK.
In this communication model, EIV alert and trace data is transported first via the existing communication channel to the intermediary system, passed to the application running the Relay function, which itself forwards the data to the Sternum Platform.
More details and examples are given in the Relay section of the Sternum SDK documentation.
Security coverage - Multi-layer defense
EIV implements adaptive and deterministic RASP-like protection for embedded devices. Leveraging binary instrumentation. It categorically prevents certain classes of code and memory manipulation attempts and assures system integrity at all times.
EIV's self-protection is augmented by the XDR-like threat detection capabilities of the Sternum Platform, which provides intelligence about indicators of exposure and compromise, ranging from unauthorized access to DDoS or brute force assaults.
By leveraging the device traces, the Sternum Platform's anomaly detection also provides a constant situational awareness of device-level issues, not only related to security but to the general device operations.
The security coverage offered by EIV and the Sternum Platform includes MITRE's 'Top 25 Most Dangerous Software Weaknesses' in scope for IoT - including command injections, execution flow manipulations, buffer overflows, and more.
This coverage is illustrated on the security wheel accessible on the Sternum Platform and illustrated (snapshot) below:
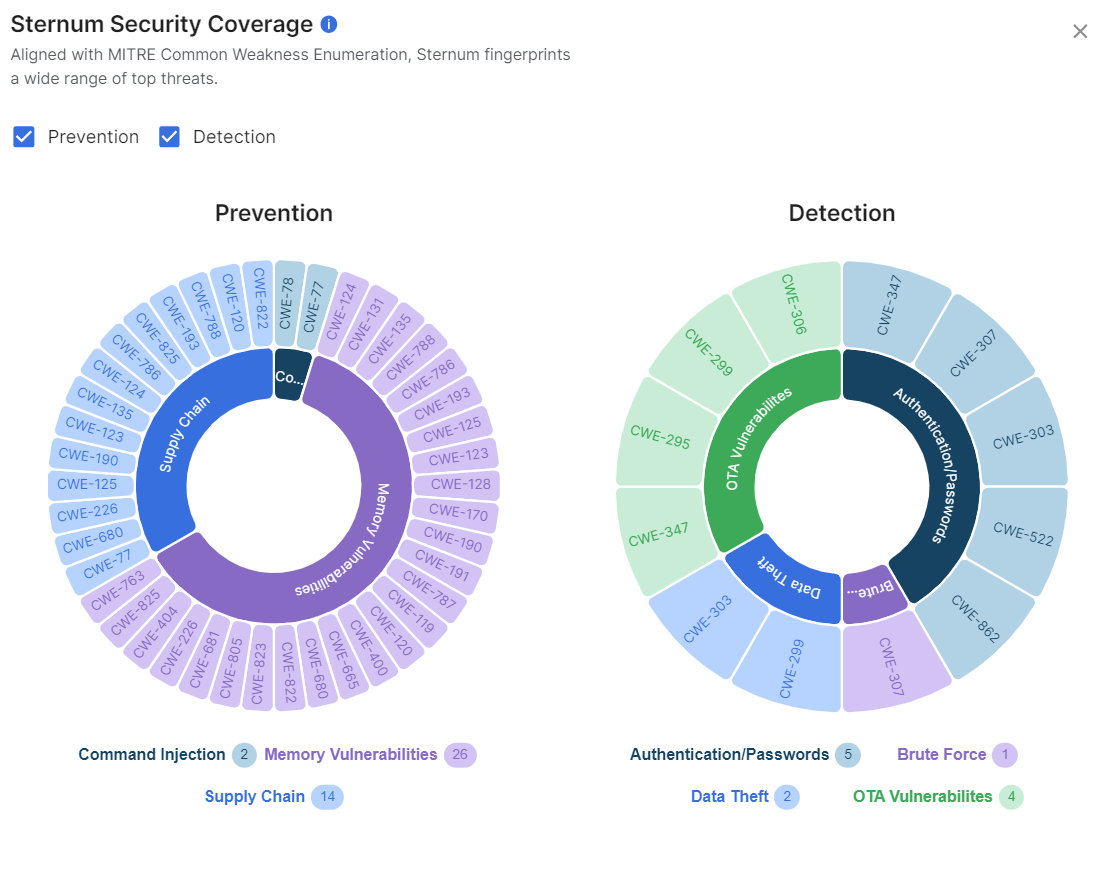
Refer to the Sternum Platform for the most up-to-date coverage information.