Overview
Sternum's Compute Security provides application runtime protection and threat detection for Linux hosts (physical or virtual machines), Kubernetes and Docker containers. Sternum leverages patented memory exploit prevention capabilities, threat detection and observability, at runtime, to protect Linux workloads, with minimal deployment effort and zero policy tuning.
Linux Runtime Protection
Sternum's patented memory protection capabilities, leveraged by the Compute Security offering, are a first of their kind, runtime compute protection solution for Linux servers, VMs, Kubernetes and Docker containers. The solution provides proactive memory integrity-based attack prevention, with visibility and monitoring of the entire host system including 3rd-party components, allowing advanced mitigation of security threats.
The Sternum memory protection capabilities use advanced binary instrumentation and hooking techniques to secure dynamic memory and critical processes in real-time. It provides simple deployment, seamless integration, low overhead and does not require any changes to the existing codebase.
Monitoring and Threat Detection
Sternum's Compute Security also leverages powerful and low impact eBPF-based monitoring and threat detection to analyze systems at runtime for suspicious behavior and threats. Deterministic rules identify anomalous and suspicious behaviors and generate security alerts which can be viewed and investigated within the Sternum Platform.
Sternum Platform
The Sternum Platform collects and analyzes security alerts and event data from protected Linux workloads and provides monitoring, dashboards, and alerting capabilities.
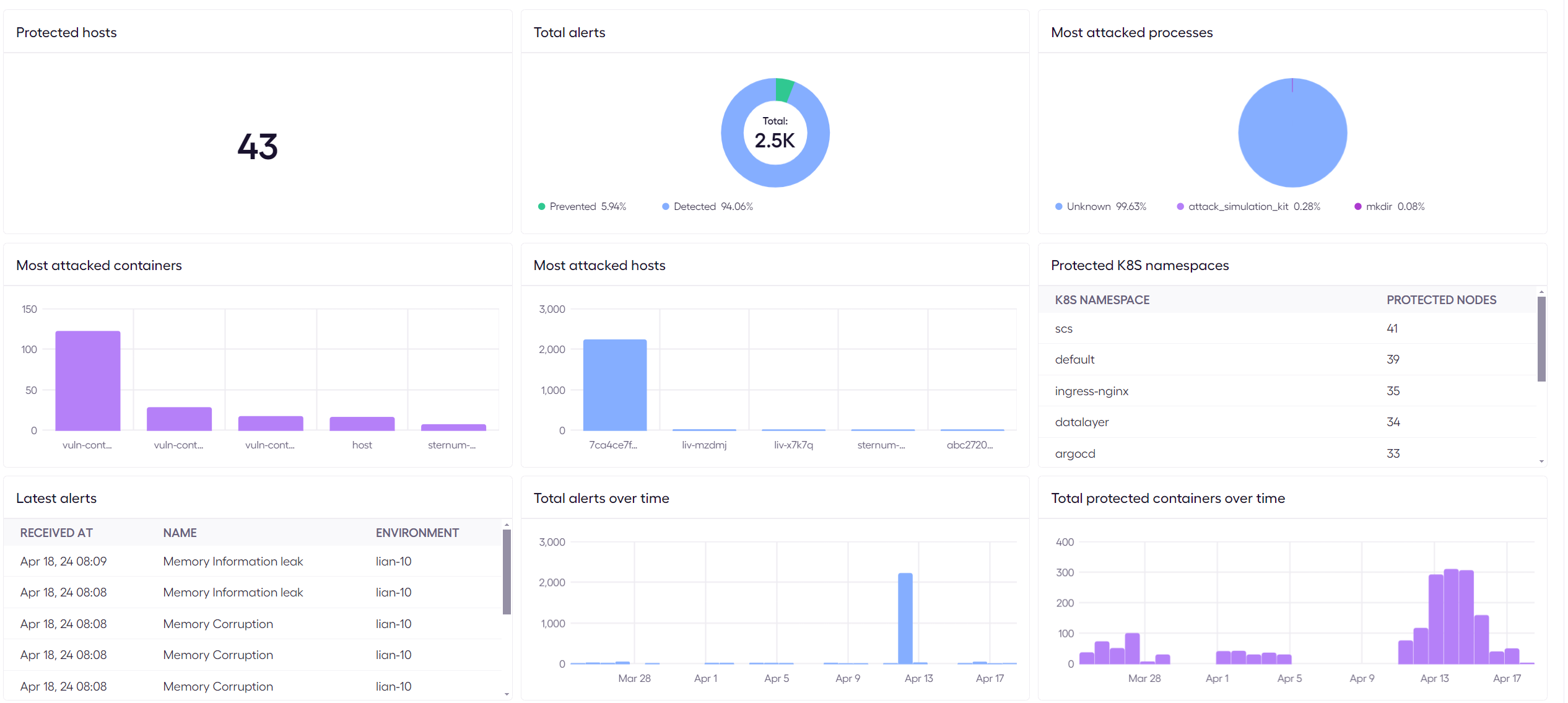
Refer to the Cloud Platform section for more details.